Important Dates
April 30th – Call for Papers closes
May 1st – June 30th – Voting period
1st week of July – Final agenda announced
____________________________
We are looking for 60-minute, offensive and defensive focused deep-knowledge presentations. Research that is new, novel and preferably material that has not been presented elsewhere prior.
If you are a woman in IT, you are strongly encouraged to apply.
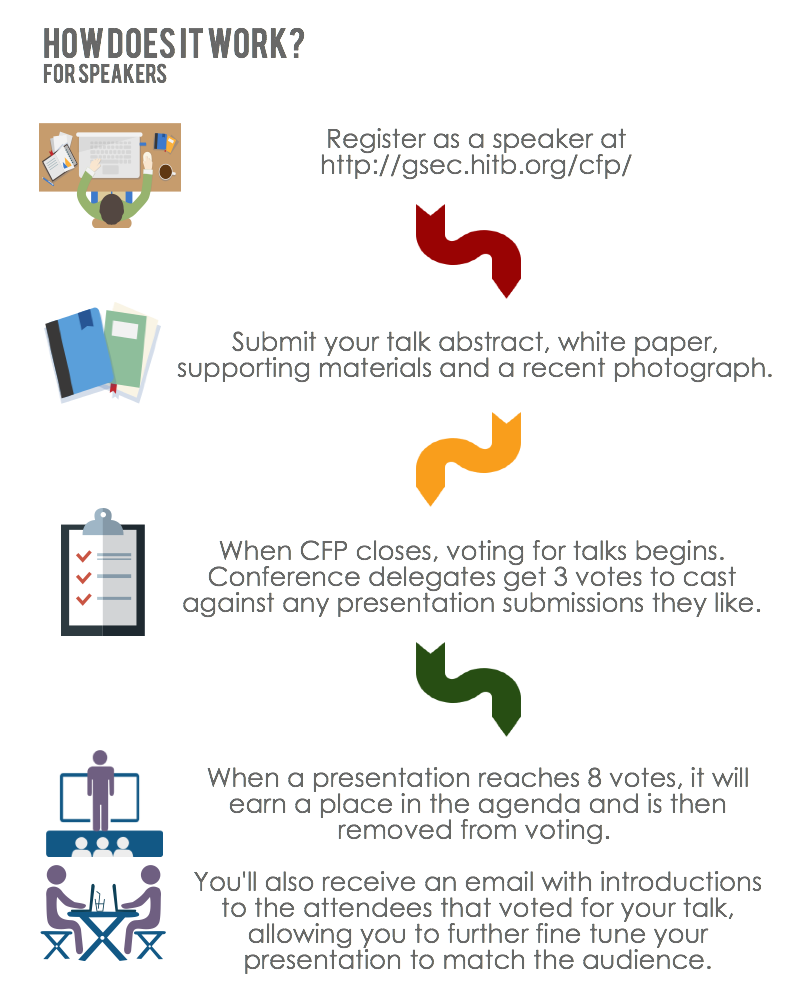
____________________________
Each accepted submission will entitle speaker(s) to:
-
- Accommodation for 3 nights / 4 days
- Travel expense reimbursement up to USD1500.00 per slot for non-resident speakers
- A USD1500 honorarium per slot
Topics of interest include, but are not limited to the following:
- Cloud Security
- File System Security
- 3G/4G/WIMAX Security
- SS7/GSM/VoIP Security
- Security of Medical Devices
- Critical Infrastructure Security
- Smartphone / MobileSecurity
- Smart Card and Physical Security
- Network Protocols, Analysis and Attacks
- Applications of Cryptographic Techniques
- Side Channel Analysis of Hardware Devices
- Analysis of Malicious Code / Viruses / Malware
- Data Recovery, Forensics and Incident Response
- Hardware based attacks and reverse engineering
- Windows / Linux / OS X / *NIX Security Vulnerbilities
- Artificial Intelligence / Machine Learning for Security
- Next Generation Exploit and Exploit Mitigation Techniques
- NFC, WLAN, GPS, HAM Radio, Satellite, RFID and Bluetooth Security
